Authy Vulnerability Exposed, 2FA Users Affected
During security testing a vulnerability was exposed on the Authy app, a two-factor authentication tool. Less than 0.2% of Authy users were affected. An outside security research team discovered the vulnerability which affects users who changed the phone number on Authy accounts since February 2014. The users affected were no longer able to access their original phone and so thus had to prove phone ownership. This process included government issued ID’s. Authy immediately moved to patch the vulnerability and has no evidence the vulnerability was exploited by nefarious characters. Authy sent....
Related News
Balancer, a decentralized finance (DeFi) protocol operating on the Ethereum blockchain, has recently disclosed a critical vulnerability impacting several of their V2 Pools. While emergency measures have been implemented successfully to safeguard a significant portion of Total Value Locked (TVL), a portion of funds remains at risk. As a precautionary measure, Balancer Labs advises users to withdraw their affected Liquidity Provider (LP) funds without delay. It is important to note that, at present, no funds have been lost, and the vulnerability has not been exploited. Related Reading:....
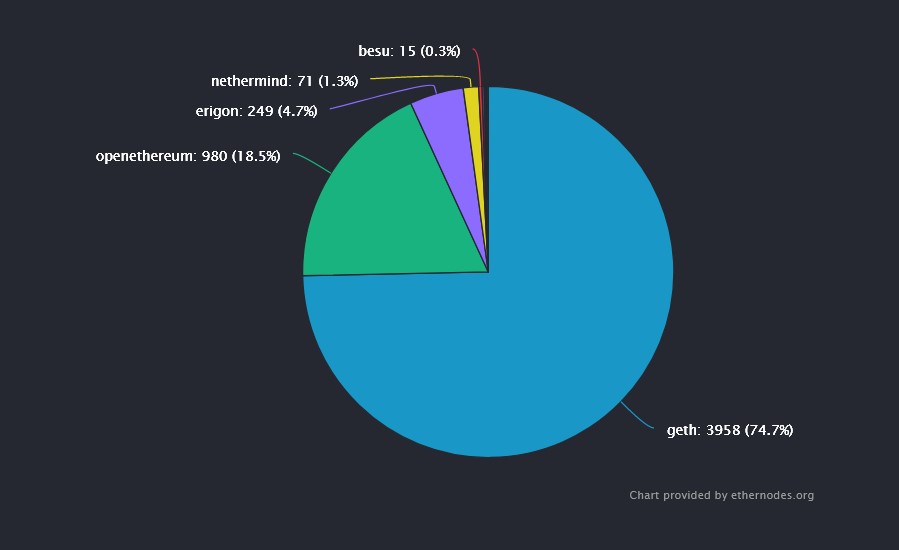
The Ethereum network is facing a chain split after an exploit forced over 50% of its nodes to upgrade their client to prevent further attacks. This security vulnerability was detected, reported, and fixed by Go Ethereum, developers of the affected client, Geth. On August 24th, 2021, via their official Twitter handle, Go Ethereum and its […]
In a disheartening turn of events, the decentralized finance (DeFi) protocol Balancer (BAL) confirmed a hack just days after warning about a critical vulnerability impacting multiple Pools. The attack, which took place on August 27, resulted in a loss of nearly $1 million for Balancer. Previously, on August 22, NewsBTC reported that Balancer had discovered a critical vulnerability affecting its protocol. However, despite efforts to mitigate the risks and caution users, Balancer could not pause the affected pools. In response, the protocol urged users to withdraw from the impacted liquidity....
Multiple versions of Android are vulnerable to Dirty Cow, regardless of device manufacturer. Even though mobile devices are becoming more popular than ever before, there are still systemic risks. Mainly the Android operating system seems vulnerable to more attacks than ever before. Dirty Cow, a new vulnerability discovered this week, may affect a lot of Bitcoin users as well. One can never be too careful when dealing with finances. It is not the first time a new Android vulnerability is discovered. Given the sheer popularity of this mobile operating system, hackers have been attracted to....
The vulnerability in private keys generated by the popular Profanity vanity key generator was noted in January and has already been implicated in at least one major hack. Blockchain cybersecurity company Certik has said a vulnerable private key was attacked in the Wintermute hack. A vulnerability in private keys generated by the Profanity app was likely exploited. The vulnerability has been known since at least January.The U.K.-based algorithmic crypto market maker announced the hack on Tuesday and said over-the-counter and centralized finance operations were not affected. About $162.5....