Selfish Mining: A 25% Attack Against the Bitcoin Network
One of Bitcoin's core security guarantees is that, for an attacker to be able to successfully interfere with the Bitcoin network and block and reverse transactions, they need to have more computing power than the rest of the Bitcoin network combined. The reason for this is that the Bitcoin network builds up its transaction history in the form of a....
Related News
A paper released yesterday by researchers Ittay Eyal and Emin Gun Sirer at Cornell University suggested a subtle new way in which the bitcoin mining network could be vulnerable to a form of economic attack called 'Selfish Mining'. Gavin Andresen, the lead developer of Bitcoin, was quick to dismiss the paper and its contents. Executive summary of Cornell paper: not a big deal even assuming their analysis is correct (I'm not yet convinced). - Gavin Andresen (@gavinandresen) November 5, 2013. Although a similar attack called the 'Mining Cartel Attack' was proposed as early as 2010, the new....
It is generally accepted that latency in block propagation is one of the bottlenecks for Bitcoin scaling. This is why many of Bitcoin’s most active developers and researchers have presented a series of solutions to compress blocks and speed up propagationover the past years. It is not as well known that these solutions may not suffice on their own. Due to a practice called “spy mining” or “pool-watcher mining,” Bitcoin mining has increasingly come to rely on the data and network infrastructure provided by mining pools. As a result, many mining pools are not necessarily incentivized to....
Assuming you haven't already heard of a paper released by two researchers at Cornell University yesterday that suggested the Bitcoin currency is susceptible to a little something called 'selfish mining,' I will do my best to give you the Spark Notes version. The paper - put together by Ittay Eyal and Emin Gun Sirer - explains that rogue mining pools could possibly keep the discovery of a Bitcoin block private whilst other mining pools look for that very same block - expending mining resources. The point in keeping the block private is to allow the described 'selfish' mining pool to get....
A 51% attack occurs when a miner (or miners) acquires more than 50% of the network's mining hash power and takes control of the network,
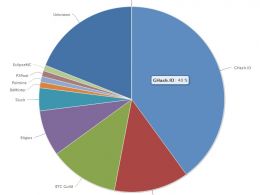
Many are uncomfortable with Ghash.io's large percentage of total network hashrate. Update: Ghash.io has responded as expected. Two Cornell researchers that have been trying to poke holes in Bitcoin's network security, Ittay Eyal and Emin Gün Sirer, have taken this opportunity to remind the Bitcoin community of many other theoretical attacks that can occur with a centralized Bitcoin mining network. In fact, many of the theoretical attacks described would arguably be more likely than a blatant 51% attack. However, any attack, no matter how subtle, could be detected on the blockchain and the....