Source Code for Mirai Internet of Things Botnet Appears Online
To put this potential into perspective, Mirai is capable of pulling in several hundreds of thousands of bots from IoT devices. Security researchers have come across the source code for the Internet of Things botnet called Mirai. This botnet has been used to launch major DDoS attacks against various websites. Such a powerful tool could be used to shut down nearly any public website in existence today. Now that the source code has been leaked, it becomes a lot easier to render the botnet useless. Connecting millions of devices to the Internet sounds great on paper, but it creates a big....
Related News
The original files of the internet source code for the World Wide Web were sold Wednesday as a nonfungible token, or NFT, for $5.4 million, the latest in a string of NFTs to fetch upward of a million dollars. Tim Berners-Lee Sells Internet Source Code The original source code for the internet as we […]
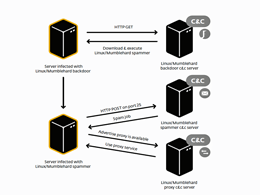
For many years, people assumed lInux was one of the most secure operating systems in the world. Even though the number of cyber attacks against Linux machines remains relatively small for now, several thousand machines were infected with malware, forcing them to send out spam messages. As we all know, spam messages – such as the ones sent through Mumblehard – are one of the more common causes of Bitcoin ransomware infections. Mumblehard Linux Spam Botnet is No More. It has been over a year in the making, but Estonian law enforcement and the Eset security firm managed to put an end to the....
Facebook has successfully dismantled a major bitcoin botnet operated by a small team of cyber criminals based in Greece. The Lecpetex botnet managed to infect 250,000 computers. At its peak it compromised as many as 50,000 Facebook accounts. Lecpetex propagated through the social media platform using spam messages with malicious code inserted into zipped attachments. Each zip archive contained an embedded Java file that would download and install a litecoin miner. It would also steal cookies and gain access to the victim's friend list, using it to send out even more spam. However, mining....
It was just last month that IBM's plans for an "Internet of things" architecture that would feature Bitcoin blockchain technology were revealed. IBM's planned project, called Adept, utilizes three distinct technologies including the blockchain, TeleHash, and BitTorrent. IBM's head of mobile and internet Paul Brody is the "VP of the Internet of Things" and is in charge of the project. In a recent talk with Gigaom at their Structure Connect event in San Francisco, Brody further explained his vision for the Internet of Things and he emphasized that developers should welcome open-source....
Locky remains one of the biggest ransomware threats to this very date. Now that the Necurs botnet is back, it looks like a new version of Locky Bitcoin ransomware is available as well. A new spam campaign is underway to infect as many computers as possible. Roughly three weeks ago, the Necurs botnet suddenly went offline, leaving security researchers puzzled as to what happened to it. This reprieve was rather short-lived, however, as the botnet returned in full force a few days ago. Moreover, it is spreading an improved version of both Locky ransomware and the Dridex banking trojan. Necurs....