KnowBe4 Warns: Third Ransomware Strain Called CryptorBit Attacks
Infections with this recent CryptorBit strain are on the rise, and once a user's files are encrypted, the fees are up to $500 ransom in bitcoin to decrypt the files.
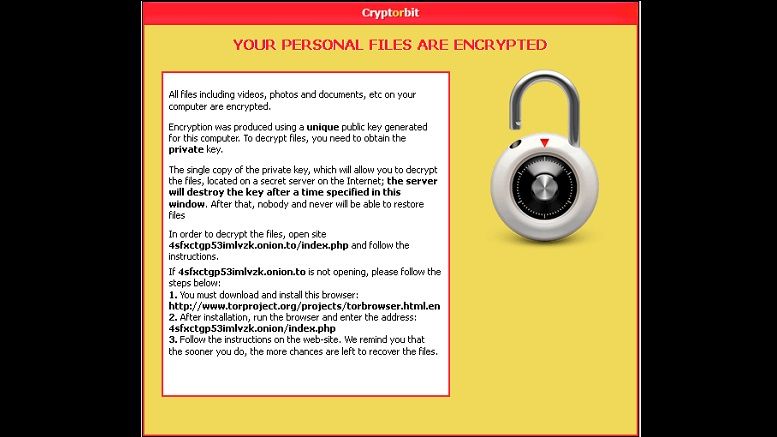
Security Awareness Training expert KnowBe4 issued a warning of a third criminal ransomware gang ramping up their attacks. The malware is called CryptorBit, (also known as HowDecrypt), and follows a very similar attack process as CryptoLocker and CryptoDefense, but the malware corrupts the first 512 or 1024 bytes of -any- data file it finds, regardless of extension increasing its potential to wreak havoc. The cyber gang uses social engineering to get the end-user to install the ransomware using a fake Flash update, or install a rogue antivirus product.
“Infections with this recent CryptorBit strain are on the rise, and once a user's files are encrypted, the fees are up to $500 ransom in bitcoin to decrypt the files,” said Stu Sjouwerman, CEO of KnowBe4.
It was initially released December 2013, and after debugging their criminal infrastructure, attacks are now increasing. Moreover, users can’t rely on antivirus since it catches less than 50% and “antivirus is dead” according to Symantec.
The CryptorBit ransomware comes with extra features. It appears to bypass Group Policy settings that were put in place to defend against this type of ransomware infection. The cybercriminals are also installing so-called cryptocoin miner software which utilizes the victim's computer to mine digital coins such as Bitcoin, which will get deposited in the malware developer's digital wallet, making them even more money according to bleepingcomputer.com
When a workstation is infected, the bad guys want you to install the Tor Browser, enter your address, and follow instructions on their website how to pay. They leave a friendly reminder that the sooner you pay, the more chance you have to "recover the files". Once you pay, supposedly you get their CryptorBit Decryptor program. Based on the payments sent to known CryptorBit Bitcoin addresses, quite a few people appear to have paid the ransom. The price can double after the first 96 hours (4 days).
Sjouwerman gives these tips to prevent the loss of data;
1) Backup, backup, backup and test your restore procedure on a very regular basis.
2) Don’t rely on just antivirus as they normally run 6 hours behind attacks like this, enough for the bad guys to get in and wreak havoc. See Virus Bulletin’s testing info.
3) Don’t open anything suspicious. Use extra care to avoid phishing links and attachments. If you didn’t request it, don’t open it.
4) If you do fall prey to CryptorBit, wipe the infected machine(s), rebuild from the ground up, and restore the files from the most recent backup. If there are no backups, try to restore the files from Shadow Volume Copies. If these are not available, you can try a utility called DecrypterFixer written by Nathan Scott.
With malware like this out there, security education and behavior management is a must for any organization where users have access to email and the web.
To learn more visit http://www.knowbe4.com/
About Stu Sjouwerman and KnowBe4
Stu Sjouwerman (pronounced “shower-man”) is the founder and CEO of KnowBe4, LLC, which provides web-based Security Awareness Training (employee security education and behavior management) to small and medium-sized enterprises. A data security expert with more than 30 years in the IT industry, Sjouwerman was the co-founder of Inc. 500 company Sunbelt Software, an award-winning anti-malware software company that he and his partner sold to GFI Software in 2010. Realizing that the human element of security was being seriously neglected, Sjouwerman decided to help entrepreneurs tackle cybercrime tactics through advanced security awareness training. KnowBe4 services hundreds of customers in a variety of industries, including highly-regulated fields such as healthcare, finance and insurance and is experiencing explosive growth with a surge of 427% in 2013 alone. Sjouwerman is the author of four books, with his latest being Cyberheist: The Biggest Financial Threat Facing American Businesses.
Tags: Ransomware, CryptoLocker, CryptorBit, Security Awareness Training, Phishing
Related News





