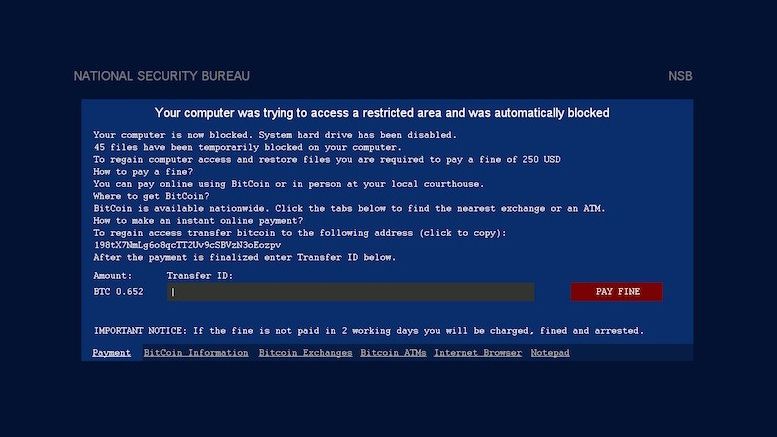
New Hybrid VirRansom: The AIDS of Ransomware on the Loose
KnowBe4 CEO Stu Sjouwerman issued a warning of a scary new strain of ransomware, one with a difference, this one is a true self-replicating parasitic virus called VirRansom. This new strain is a hybrid that combines CryptoLocker and http:// CryptoWall functionality with active self-replicating virus infections of all the files it can find. And like the cybercrime Reveton family of malware, it locks the PC's main screen demanding 0.619 Bitcoin to let you back in.
Sjouwerman stated, “This ransomware threat utilizes both ransomware and parasitic virus features. VirRansom is a full fledged virus which will spread across your network and doing a less than perfect job on the disinfection can easily lead to reinfection of your whole network. CryptoWall-encrypted files that you can't or don't decrypt are harmless garbage forever, but you can delete those. However, with VirRansom, files that you don't decrypt are still recoverable, but remain actively infectious.” Sjouwerman added; “What makes this tricky is the infected files can't just be deleted, since they are your own files that were there before the infection started.”
According to researchers at Sophos, most worms leave a handful of infected files that weren't there before and need to be deleted. Parasitic viruses, in contrast, may leave hundreds or thousands of infected files on each computer. If even one of those infected files are left behind after a clean-up, the infection will start up all over again.
The file encryption is not as advanced as CryptoWall. For now, the key to decrypt the files is contained in the malware itself. Most antivirus should soon be able to decrypt the files and restore them, but the bad guys are constantly changing encryption keys in which case antivirus vendors may not be able to solve this fast enough...
Sjouwerman cautioned, “Ransomware gets nastier all the time. We can expect a VirRansom 2.0 with "new features" like industrial-strength CryptoWall-like encryption where files are held hostage until payment is made and email server infections where emails are converted to a worm for maximum dissemination of their malicious code. The legal ramifications could be horrific.”
Sjouwerman suggests IT managers mitigate these types of threats through both technical measures and enforcing security policy, such as:
1. Test the Restore function of your backups and make sure it works and have a full set of backups offsite.
2. Start thinking about asynchronous real-time backups so you can restore files with a few mouse clicks.
3. Get rid of mapped drives and use UNC (universal naming convention) links for shared folders.
4. Look into Whitelisting software that only allows known-good executables to run.
5. Update or enforce security policy best practices, such as thorough effective security awareness training to prevent these types of infections to begin with, as the infection vector is your end-user opening up an attachment or clicking on a link.
About Stu Sjouwerman and KnowBe4
Stu Sjouwerman (pronounced “shower-man”) is the founder and CEO of KnowBe4, LLC, which provides web-based Security Awareness Training (employee security education and behavior management) to small and medium-sized enterprises. A data security expert with more than 30 years in the IT industry, Sjouwerman was the co-founder of Inc. 500 company Sunbelt Software, an award-winning anti-malware software company that he and his partner sold to GFI Software in 2010. Realizing that the human element of security was being seriously neglected, Sjouwerman decided to help entrepreneurs tackle cybercrime tactics through advanced security awareness training.
KnowBe4 services hundreds of customers in a variety of industries, including highly-regulated fields such as healthcare, finance and insurance and is experiencing explosive growth with a surge of 427% in 2013 alone. Sjouwerman is the author of four books, with his latest being Cyberheist: The Biggest Financial Threat Facing American Businesses.
For more information about Stu Sjouwerman and KnowBe4visit: http://www.KnowBe4.com/
About Kevin Mitnick
Kevin Mitnick is an internationally recognized computer security expert with extensive experience in exposing the vulnerabilities of complex operating systems and telecommunications devices. He gained notoriety as a highly skilled hacker who penetrated some of the most resilient computer systems ever developed. Today, Mitnick
Related News





