Malware Evolution: New Ransomware Variants Like CryptoLocker Cost Users Some Serious (Bit)Coin
Ramsomware like CryptoLocker can leave you in a very bad spot. There’s no doubt about it, threats like CryptoLocker have the potential to devastate individual users and businesses alike.
Encryption is a word that is supposed to bring peace of mind to computer users. It’s supposed to mean sensitive data will be protected from the prying eyes and/or control of unwelcome visitors. CryptoLocker, a recent variant of malware known as ransomware, is flipping that notion on its head by leveraging encryption to hold a victim's data hostage until the hacker’s ransom demands are met. Joe Caruso, founder and CEO/CTO of Global Digital Forensics, a premier provider of cyber security solutions, took some time to weigh in on this latest trend in ransomware, and shares some tips on how to significantly boost the chances of thwarting threats like these.
CryptoLocker packs a big punch.
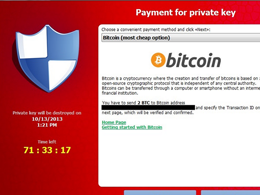
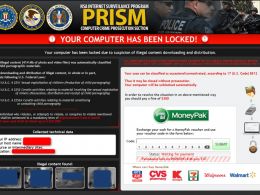
“There’s no doubt about it, threats like CryptoLocker have the potential to devastate individual users and businesses alike, because by the time this ransomware pops up its notice that your data is being held for ransom, its work is already done. In CryptoLocker’s case, that means nothing can be done at that point except to either restore from the most current backups you have, hopefully, or pay the ransom and cross your fingers that you will actually be sent the key needed to decrypt all the affected files. And to make the decision even more nerve wracking, the pop-up notification screen starts a countdown clock, usually between 72 and 100 hours, stating that once it hits zero, the key you need will be deleted forever - and with it, any hope of ever seeing your data again. Although, some recent reports seem to point to the possibility that hackers may have rethought that last part and there still may be a way to retrieve the key after the time limit expires. They may have realized many people find it difficult to figure out how to purchase Bitcoins or do MoneyPak transactions within the allotted time and they felt they were leaving a lot of cash in the wind, but these are criminals after all, so it could also just be a last ditch effort to get their payment even after the hostage is dead.”
How does CryptoLocker work?
“Once you’ve been infected with CryptoLocker, it encrypts every file it finds with the file extensions it’s built to target, like documents, pictures, spreadsheets and a host of other file types important to most users. It can also spread across shared networks and even shared NAS (Network Attached Storage) drives on a VM (Virtual Machine), encrypting all those files too, which is a catastrophic situation for any business. It uses two phases, first it encrypts everything with a locally stored 2048-bit RSA encryption key and then it encrypts those encrypted files again with a 256-bit AES encryption key which is stored on the hacker’s command and control server, giving them total control over ever getting the encryption unraveled. So the key masters can now demand whatever they want. Unfortunately, our dependency on digital information today also means they’ll often get it.”
Will paying the ransom get the decryption key?
“It’s a crapshoot – cyber criminals are not the most trustworthy bunch, but if you don’t have good backups, it may be the only “desperate times” measure you have left. Some of those infected report they got the key after they paid the roughly $300 ransom equivalent by purchasing 2 Bitcoins or sending payment through a MoneyPak prepaid card, and others did not get a key. And don’t count on tracing the transaction, using anonymous currency alternatives like Bitcoins and MoneyPak have long been favorites of ransomware designers because they are effectively as hard to trace as cash.”
How is CryptoLocker delivered?
“The most common way is through a phishing email with an infected attachment, but Driveby attacks launched from visited websites containing malware are also used. ”
How can ransomware like CryptoLocker be avoided?
“In two words, vigilance and awareness. Automated antivirus and antimalware solutions can do an excellent job stopping a great majority of attacks, but they are not intelligent enough to deal with the social engineering strategies hackers use today to compromise targets. And the key to stopping threats like CryptoLocker, is to never receive the payload in the first place. Hacks that make national news, and a majority of big ones that go unreported for obvious reasons, almost always use some type of social engineering geared to target the weakest link in any security chain, the human element. Whether it’s one individual in an organization falling for a phishing or spear phishing email and opening the doors for a hacker to exploit an entire network, or a hand delivered payload getting injected via an infected USB stick, stopping the most advanced and costly threats all starts with understanding what to look for, where the weak links are and how to avoid becoming a victim. That’s what we do for clients with comprehensive penetration testing, with a special focus on social engineering methods used by today’s real-world hackers, and we’ve done pen-testing for hundreds of organizations, including companies and corporations recognized around the world.”
What exactly is penetration testing (pen-testing)?
“Penetration testing basically means we put on the black hat and try to compromise a company the same way a hacker would. We will design and launch sophisticated spear phishing campaigns, dummy websites and all. We’ll try to get “infected” USB sticks plugged in to a system on the network by planting them in common areas to see who takes the bait, and we’ll even impersonate technicians or other personnel to see if we can deliver a payload that way, along with every other clever bit of tradecraft we’ve seen successfully used over the years. We even developed the C-All User Activity Monitor/Recorder which works like a video surveillance system for a network. Not only can it be used by IT security personnel to monitor and record activity and send email notifications when customized “triggers” are activated, but it also works as a great training tool by allowing managers and/or security to see how users behave and what mistakes they make . And when employees are made aware of its presence, they tend to really watch their Ps and Qs, which automatically stiffens security against advanced cyber threats relying on human failure. It’s also a great way for security to regularly pinpoint what kind of awareness training is needed to improve the organization’s overall cyber security posture.”
Global Digital Forensics
Global Digital Forensics is a recognized industry leader in the fields of computer forensics services, electronic discovery (eDiscovery), cyber security and emergency incident response, with years of experience assisting clients in the government, banking, healthcare, education and corporate arenas. For a free consultation with a Global Digital Forensics specialist, call 1-800-868-8189 about tailoring a plan which will meet your unique needs. Emergency responders are also standing by 24/7 to handle intrusion and data breach emergencies whenever and wherever they arise. Time is critical if a cyber-incident has occurred, so don’t hesitate to get help.
For more information about Global Digital Forensics, visit http://www.evestigate.com/
Related News